Hot Wallets vs Cold Wallets: Key Differences Explained
The biggest differences between crypto hot and cold wallets are their security, use cases, and the level of convenience they offer. Most traders and investors’ first experience of using crypto begins with one of these types of wallets.
Cold and hot wallets are about as different as their names imply. In this guide, you’ll learn what they are, the different types of each, how they work, and what and who each is most useful for.
Hot Wallets vs Cold Wallets: Key Takeaways
- Cold wallets are better suited for long-term storage of a high-value portfolio, while hot wallets are more useful for those who make frequent on-chain transactions.
- There are many types of hot wallets and two types of cold wallets. Each offers different levels of security and convenience.
- The biggest differences between hot and cold wallets are private key storage, price, user experience, and security.
- Choosing a wallet isn’t a matter of which is best; rather, it’s a question of which wallet is better suited for your purposes.
What are Hot Crypto Wallets?
Crypto hot wallets are software applications that maintain a constant connection to the internet and store your private keys on internet-connected devices. Think of “hot” in terms of activity – you access them more frequently.
Hot wallets are usually free, convenient to use, and you can use them via your mobile device, tablet, PC, or browser.
According to data from Coinlaw and Future Market Insights, hot wallets are expected to account for approximately 61-69% of the crypto wallet market by the end of 2025. This trend aligns with the accessibility of hot wallets: because they have a lower barrier to entry compared to their counterpart, hot wallets are more widely used in crypto.
These types of wallets are coveted by users who make frequent on-chain transactions. As a result, many people use them to interact with decentralized finance (DeFi) and other Web3 applications.
However, this convenience is a double-edged sword. Since hot wallets maintain a constant connection to the internet, they’re more susceptible to cyber attacks and malware. Therefore, you should always exercise caution when using them.
It’s best practice to limit the amount of crypto that you hold in hot wallets. You should also rotate your wallets regularly, at least once or twice a year.
Types of Hot Crypto Wallets
There are many ways to categorize hot wallets, but the broadest way is to classify them by the platforms and devices they’re available on. Here’s a quick breakdown of the types of hot wallets:
| Hot Wallet Type | Description |
| Mobile Wallet | A mobile wallet is any wallet that you can download and use on a mobile device, such as a phone or tablet. |
| Cloud/Progressive Web Applications (PWAs) | Cloud/PWA wallets are applications that are delivered through the web and can run on all devices. |
| Desktop Wallets | Desktop wallets are applications that you download and store on your personal computer. |
| Command-Line Wallet | Command-line wallets are wallets that you operate through a command-line interface (CLI), such as Terminal or PowerShell |
| Browser Extension | These wallets are browser add-ons or “extensions.” They allow you to manage your cryptocurrency from your browser. |
As we mentioned earlier, different wallet types offer varying levels of security and convenience. We typically think of hardware wallets as more secure than hot wallets, but even hot wallets have different levels of security. It’s more of a spectrum than a progressive scale of being more or less secure.
For instance, browser extensions and PWAs would be less secure than mobile and desktop wallets. The browser extension’s proximity to the web makes it more susceptible to malware. Likewise, PWAs are maintained in the cloud by a counterparty, which makes them somewhat less self-custodial.
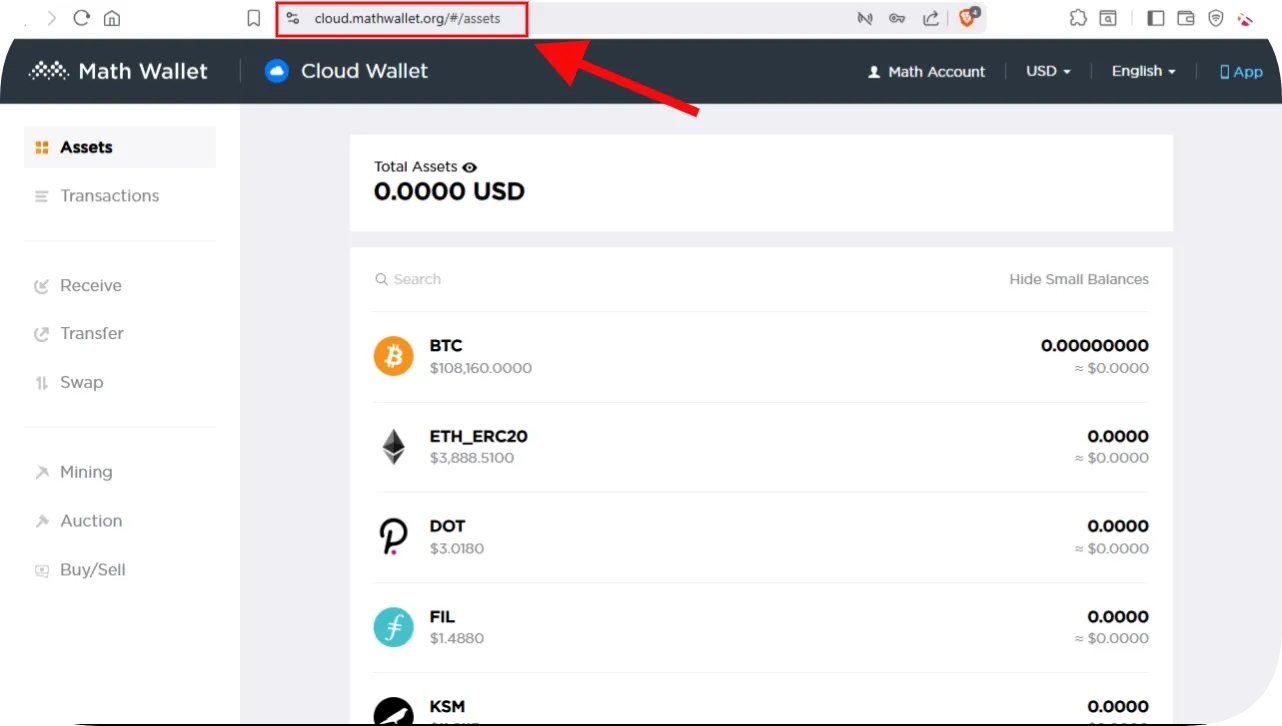
If you’re still confused about the many types of wallets and how we divide them, know this: there are two primary ways to categorize all hot wallets, regardless of features: custodial and non-custodial.
Non-Custodial/Decentralized Wallets
Simply put, a non-custodial wallet is any wallet where the user has access, holds, and controls their own private keys without any counterparties.
However, there isn’t really a universal definition for a non-custodial or decentralized wallet, despite what some may think. They more so satisfy a list of properties. That is, decentralized non-custodial wallets must:
- Hold the private keys of the client (wallet) locally
- Not hold a copy or share of the private keys anywhere else (such as is the case with multi-signature or MPC wallets)
- Ensure that only the user has access to any secrets (i.e., passwords, seed phrases, passkeys, private keys, biometric data, etc.)
- Allow users to sign transactions locally and broadcast them without a third party
To help you understand the many types of hot wallets, here are a few examples:
- Best Wallet: A mobile wallet for Android and iOS. It comes with a built-in decentralized exchange (DEX) and gives you in-app access to new crypto presales.
- Zengo: Both a mobile and a desktop wallet. Zengo supports NFTs and native, in-app staking. It uses biometric verification with multi-party computation cryptography for security, which eliminates the need for a seed phrase.
- Binance Wallet: Tied to the main Binance exchange app on mobile, this self-custodial wallet offers access to thousands of coins across 70+ blockchains and a wide range of decentralized applications (dApps)
- OKX Wallet: A feature-rich Web3 wallet that supports multiple blockchains. It is owned and maintained by the popular cryptocurrency exchange OKX, but it’s available separately, as a mobile app and a browser extension.
Custodial/ Centralized Wallets
A centralized or custodial wallet is any wallet where you’re not the sole holder of your private keys, or, in cryptographic terms, not the only one who has knowledge of your private keys or any other secrets.
Piggybacking off of our previous definition of non-custodial, custodial wallets may not allow you to hold your private key or seed phrase. And, if they do, a third party will retain a copy or share control. These wallets are most often managed by centralized exchanges or service providers.
Custodial wallets trade convenience for counterparty risk – if the custodian’s system is shut down, mismanaged, or compromised, your funds can be lost or frozen, even if your personal account remains secure. Here are some examples of custodial wallets:
- Margex: A centralized exchange that specializes in leveraged derivatives trading. It offers a mobile application for users to manage their accounts on the go.
- MEXC: A global cryptocurrency exchange that supports trading for over 4,000 cryptocurrencies. It has a mobile app and offers users a DEX.
- Binance: The world’s most popular cryptocurrency exchange. It supports trading for cryptocurrencies and NFTs, mining, staking, and its own proprietary blockchain.
What are Cold Crypto Wallets?
Unlike hot wallets, cold wallets are wallets that don’t maintain a constant connection to the internet and store your private keys on offline devices. If you think of “cold” in terms of data storage, cold wallets store your private keys like archived data in cold storage that you access infrequently.
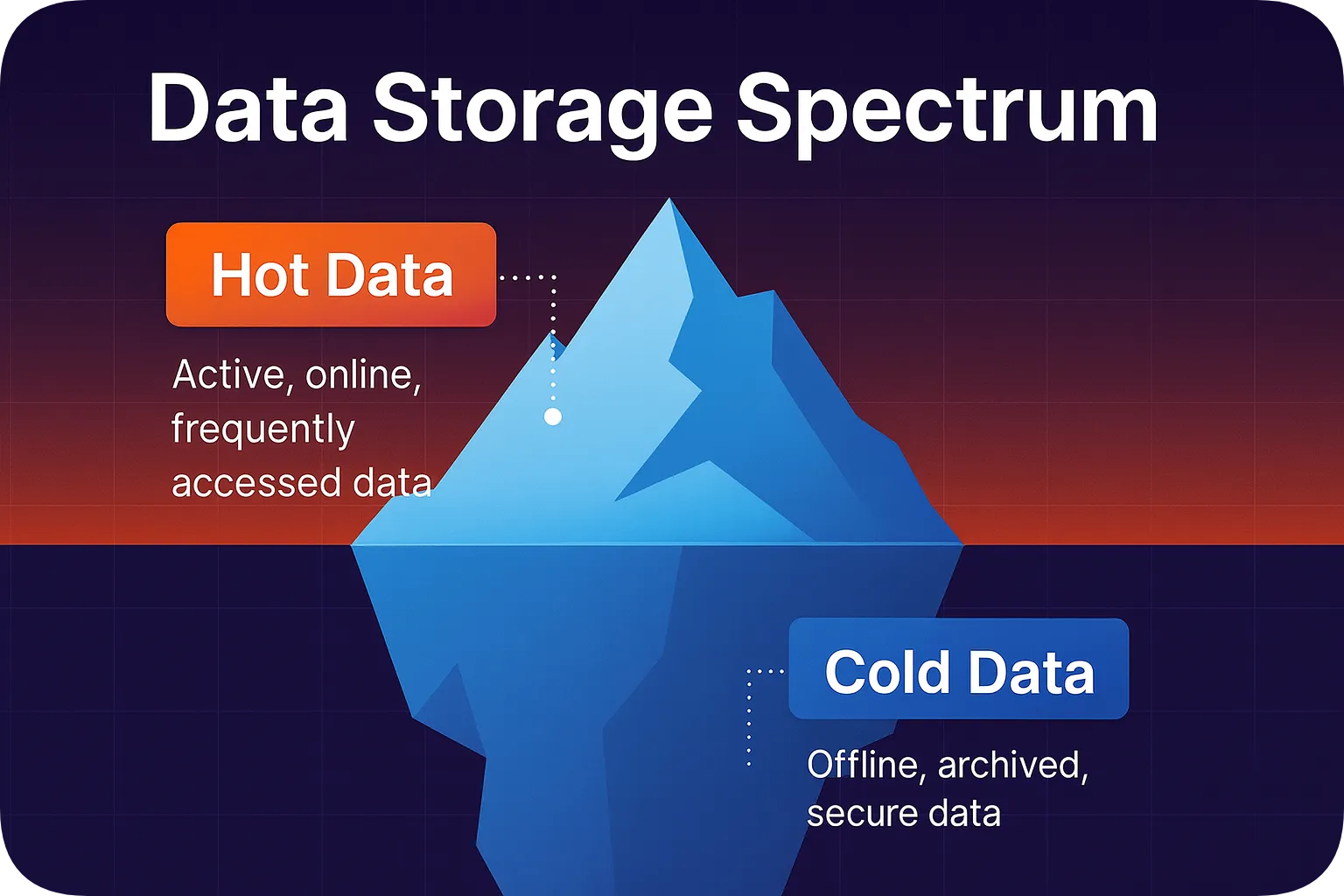
Cold wallets are much safer than hot wallets. That’s because they’re segregated by design from most vulnerabilities. People typically use them less frequently and for long-term storage of their cryptocurrency assets.
Types of Cold Crypto Wallets
Philosophically speaking, any device can be a dedicated cold wallet if it satisfies a list of properties.
There’s no globally accepted definition of a hardware wallet. Some consider a paper with 12 words a hardware wallet – after all, paper is a sort of hardware or at least not software, and the 12 words are arguably a [wallet‘s backup] – Wallet Scrutiny.
There are two main types of cold wallets: hardware and paper wallets.
Hardware Wallets
Hardware wallets are physical, portable devices that store your crypto using cold storage. They’re typically plug-in devices that resemble USB flash drives, cards, or small phones, and they usually fit in the palm of your hand.

Hardware wallets are mostly secure from online threats. They are, however, vulnerable to physical tampering. As a result, you should never purchase a hardware wallet secondhand under any circumstances.
Hardware wallets provide strong security by keeping private keys isolated from potential malware, but their overall protection can still be compromised if the connected device is infected. It’s best practice to only use them with a dedicated PC or sandboxed environment, where you limit the amount of activity that can make the device vulnerable.
Paper Wallets
As the name implies, a paper wallet is a piece of paper that holds your private keys or a QR code with your wallet information on it. This is the most secure type of cold storage — and the most inconvenient.
However, they’re not without their faults as well. Paper wallets can be vulnerable to human error, such as insecure key generation or printer leaks.
Most people don’t use them anymore because hardware wallets offer cold storage with better usability and recovery options. If you do decide to use one, you can also etch it in metal so that it lasts longer.
How do Cold Wallets Work?
Most cold wallets today are hardware wallets (people often use the term interchangeably), and they work by isolating your private keys inside a secure, tamper-resistant environment that is the device.
The idea is that your private keys never leave this environment or pass through any network connection. Instead, you sign transactions locally on the device, and only the signed data (calldata) is transmitted to the blockchain.
Many hardware wallets store your private keys inside a secure environment on the device called a secure element (SE) chip – though some also rely on alternative security architectures as well.
Some hardware wallets even go further by being air-gapped. This means that they operate without internet, Bluetooth, or NFC connections – eliminating any pathway that could expose your private keys.
Examples of Cold Crypto Wallets
Cold wallets come in many different shapes and sizes. Here are a few examples to show you how diverse the cold wallet landscape is:
- Cypherock X1: A hardware wallet that supports over 18,000 assets, comes with a three-year warranty, and uses EAL 6+ secure elements.
- Ledger: Ledger is a fintech company based in France. Known as the industry standard, Ledger uses SE technology and its own proprietary operating system.
- Tangem: A hardware wallet that resembles a credit card. It uses NFC technology to connect to a mobile device and manage your assets.
- Trezor: One of the most popular hardware wallet options, Trezor uses NDA-free EAL 6+ SE, but only for storage, to ensure even more security.
Differences Between Hot and Cold Crypto Wallets
The biggest differences between hot and cold wallets are their “proximity” to the internet, how much security they offer, and the level of convenience they provide. These differences can show up in different ways, depending on how you use your wallet. Here is a consolidated breakdown.
| Features | Hot Wallets | Cold Wallets |
| Connectivity | Constant connection to the internet | Limited connection or air-gapped from any network |
| Private Key Storage | Keys stored locally on internet-connected devices | Keys stored in a secure offline environment |
| Security | More vulnerable to malware and hacks | Highly secure against remote attacks |
| Convenience | Quick access, suitable for daily use | Less convenient, requires manual connection for transactions |
| Best For | Frequent trading | Long-term storage |
| Custody | Can be custodial or non-custodial | Always non-custodial |
| Cost | Usually free | More expensive |
Pros and Cons of Hot and Cold Crypto Wallets
There are many pros and cons of both cold and hot wallets, but the biggest ones revolve around cost, security, and ease of use.
Hot wallets are almost always free and generally easier to use, but they lack heightened security. Cold wallets are typically on the higher end, but they offer more security. Here’s a full breakdown of the pros and cons of both:
One of the more unseen benefits of owning a hot wallet is that, as time moves on, the better hot wallet security gets. Gone are the days when you’d see wallets get hacked from bad random number generation or from wallet providers saving your seed phrase in plaintext on the cloud. Today, wallet hacks make up a significantly smaller portion of cryptocurrency hacks than they used to. However, because hot wallets are software-based, they require a certain level of trust and transparency through code. For security purposes, the wallet’s entire codebase — cryptography included — should be open-source. This allows users to audit the software for safety, rather than relying on security through obscurity. Unfortunately, most hot wallets, though non-custodial, are not open-source. The biggest benefits you’ll get from owning a hardware wallet are that you don’t have to worry about remote attacks, you won’t need to rotate between multiple wallets a year, and you can often use them with hot wallets through services like WalletConnect. Hardware wallets should also be open-source, meaning their firmware and software should be publicly available. This allows users to reproduce their binaries and ensure that the compiled firmware matches the source code, protecting from hidden backdoors. To be fair, many hardware wallet manufacturers don’t follow this standard, but those that do create an additional layer of trust and security with their wallets. Therefore, most hardware wallets, though they’re probably secure, lack transparency, and we can never know for sure. For example, it’s usually advisable for beginners to stick with a custodial exchange wallet as they’re starting. Beginners can’t possibly verify calldata, manage a multi-sig wallet, navigate fractured liquidity, or anything else that ensures the safety of your cryptocurrency at a high level. For those who are more tech-savvy, a hot or hardware wallet is the next best step. As long as you keep your wallet and the devices they interact with clean, safe, and up to date, you should be okay. Then, owning both a hot and a cold wallet might be you’re best bet if you’re active in the crypto space. You can have a cold wallet for long-term storage and a hot one for daily transactions and trading. Hot wallets are for frequent on-chain activities, while cold wallets are for long-term storage. Though each one is built for certain uses, you must be careful when using both. Just because cold wallets provide extra security, it doesn’t mean that you can be lax when using them. Conversely, just because you use a hot wallet, it doesn’t mean that you’re inevitably vulnerable to hacks. Regardless of which one you choose, be safe and always practice good operational security.
Pros
Cons
Pros
Cons
Benefits and Drawbacks of Hot Wallets
Benefits and Drawbacks of Cold Wallets
Hot Wallets vs Cold Wallets: Which One Should You Use?
If you’re curious about which type of wallet you should use, the answer is simple: probably both. Let me explain. Knowing which wallet to use has more to do with knowing what you want and where you’re crypto expertise is than it does with the wallets themselves.
Conclusion
When it comes to hot wallets vs. cold wallets, many people wrongly look at them as mutually exclusive. This shouldn’t be the case, as each wallet exists for different reasons.FAQs
Can I use hot and cold wallets simultaneously?
Can cold wallets be hacked?
What happens if I lose my cold wallet?
Is Coinbase a cold or hot wallet?
Should I transfer all my crypto to a cold wallet?
Do I need a hot wallet if I have a cold wallet?
What are common cold wallet mistakes?
References
About Cryptonews
Our goal is to offer a comprehensive and objective perspective on the cryptocurrency market, enabling our readers to make informed decisions in this ever-changing landscape.
Our editorial team of more than 70 crypto professionals works to maintain the highest standards of journalism and ethics. We follow strict editorial guidelines to ensure the integrity and credibility of our content.
Whether you’re looking for breaking news, expert opinions, or market insights, Cryptonews has been your go-to destination for everything cryptocurrency since 2017.
















 Camila Karam
Camila Karam 
 Ines S. Tavares
Ines S. Tavares 
