What Are Privacy Coins? Guide to Private Crypto in 2026
Privacy coins are cryptocurrencies that allow anonymous transactions by obscuring the sender, receiver, and transaction amounts.
Most cryptocurrency networks, including Bitcoin and Ethereum, use wallet addresses as pseudonymous identities and log all transactions on a public ledger. Privacy coins offer a higher degree of anonymity by making it difficult to associate a wallet address with a real-world identity, often obscuring the transaction amount as well.
In this guide, we’ll discuss the common types of privacy coins and the methods they use to conceal transactions, making them as anonymous as cash. We’ll also explore legitimate uses for privacy coins as well as the regulatory hurdles they face. Let’s begin with some key takeaways.
Best Private Wallet for Anonymous Investing – Editor’s Choice
- Non-custodial multi-chain wallet.
- Broad ecosystem of wallet features.
- Portfolio management and market insights within the wallet.
- In This Article
- In This Article
- Show Full Guide
Key Takeaways
- Privacy coins offer similar anonymity to cash, but in digital form, allowing users to transact without leaving a trail to follow.
- Several technologies provide privacy solutions, including ring signatures, stealth addresses, and zero-knowledge proofs.
- Common use cases for privacy coins center on legitimate peer-to-peer payments, although privacy coins have been used for illicit transactions as well.
- Changes in EU AML rules will effectively ban privacy coin trading on EU-regulated crypto exchanges in 2027.
Privacy Coins Explained
Privacy coins prioritize user privacy, often by obscuring wallet addresses, balances, transaction amounts, and transaction parties. Most cryptocurrencies follow a different, less privacy-focused structure, allowing the potential for others to link a wallet address to a real-world identity.
When Bitcoin launched in 2009, it provided a decentralized and permissionless way to transfer value without an intermediary. There was no need to trust a third party to complete the transaction and no censorship to prevent certain types of transactions or limit specific users. However, to some in the cryptocurrency space, Bitcoin was still lacking a key feature: privacy.
Bitcoin and the vast majority of cryptocurrency networks use pseudonymous wallet addresses to represent user identities on the network. The nature of the blockchain allows anyone to follow the money trail as coins or tokens change hands.
Pseudonymous wallet addresses do not protect user anonymity, and anyone with enough resources and a breadcrumb trail to follow can unmask the real-world user of a typical cryptocurrency wallet address.
As a group, privacy coins set out to solve a problem without losing the key focus of permissionless and trustless transactions: Pseudonymity ≠ anonymity.
Privacy coins also use wallet addresses, but they employ various strategies to obscure visible transaction data, making it difficult or impossible to link a specific transaction to a real-world identity. Privacy coins prioritize anonymity, often by default, and in some cases, on demand.
Bytecoin was the first privacy coin, launched in 2012, and it eventually led to the launch of Monero in 2014, which remains the leading privacy coin.
Are Privacy Coins Really Private?
Privacy coins promise anonymity, but no protocol can guarantee 100% privacy. A flaw in the protocol may be discovered, or users themselves may provide details that could aid a determined sleuth seeking to unravel a transaction’s details.
Various privacy coin projects employ a range of techniques to allow anonymous transactions, and in some cases, privacy is an on-demand feature. For example, Zcash offers optional privacy, whereas Monero makes all transactions private.
While privacy coins like Monero make on-chain analysis extremely difficult, blockchain analytics may still reveal clues. Protocols like Zcash make it easier to view transactions between private and public addresses. However, the biggest exposure often comes from interacting with a wallet address that’s linked to a real-world identity, such as a crypto exchange. A withdrawal from a crypto exchange that knows your identity to a non-custodial wallet address provides a starting point for government agencies or others who may have access to your identification information on the exchange.
How Does a Privacy Coin Work?
Most blockchains make transactions publicly available on an open ledger. For example, when using Bitcoin, anyone can see the transaction amount, the sender’s wallet address, and the receiver’s wallet address for a given transaction. The balances of these wallets are also visible, as are the balances and transactions of all the wallet addresses they have interacted with.
One piece of information, such as an identity linked through an exchange, employer, or customer, can provide a map to the now-deanonymized user’s blockchain history.
Privacy coins address these concerns by using various techniques to obscure sender and receiver addresses, transaction amounts, or all of these potentially revealing details.
Let’s explore the common methods used by some popular privacy coin protocols.
Ring Signatures (Monero)
The leading privacy coin, Monero, uses ring signatures to obscure the wallet address that signed a transaction. The protocol groups the real signer with a group of 15 or more decoy public addresses (the ring), any of which can appear to be the signer. Anonymity depends on the size of the ring, with larger rings making it more difficult to determine who signed the transaction.
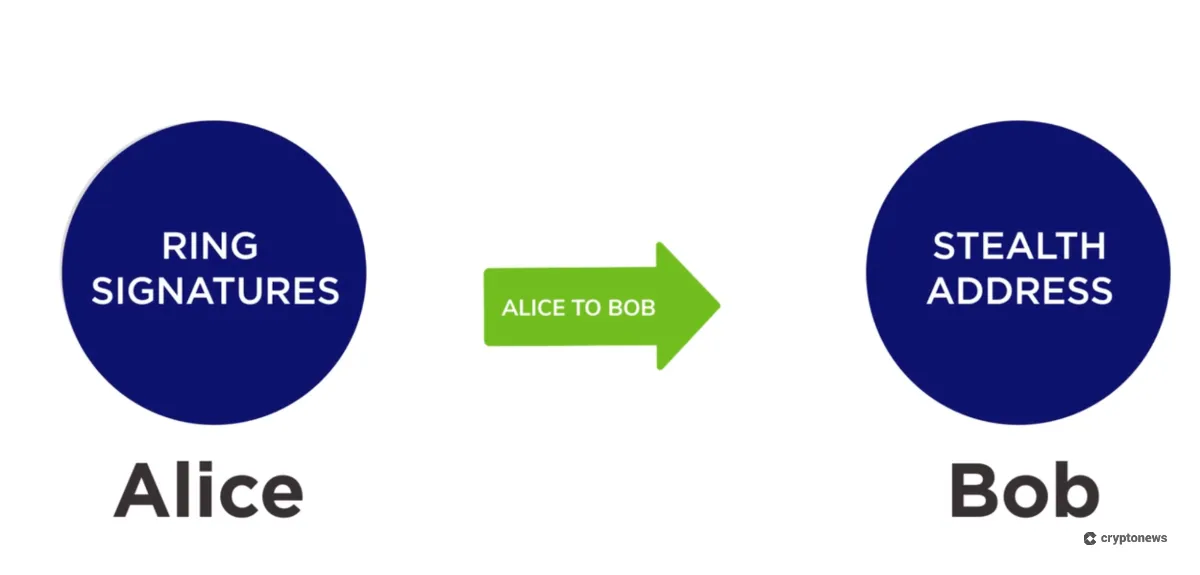
Monero combines ring signatures with stealth addresses to obscure the receiver’s wallet address and RingCT (Ring Confidential Transactions) to obscure the transaction amounts.
Stealth/One-Time Addresses
A stealth address acts as a one-time alias for the receiver. For example, Monero generates a unique wallet address for each transaction, which is visible on the blockchain but not publicly linked to other wallet addresses owned by the recipient. The receiver provides a public address to the sender, and the protocol automatically creates a stealth address. These stealth address funds remain spendable. When sending, the user’s Monero wallet scans the network for addresses it can access, allowing the user to sign transactions for the stealth wallet address.
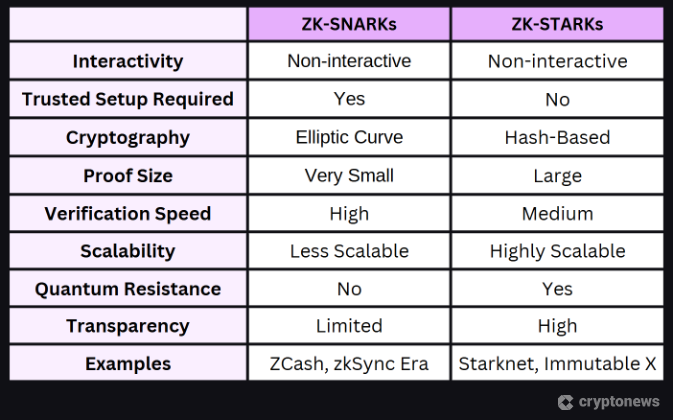
Protocols like Zcash use zk-SNARKs to protect privacy, whereas Aleph Zero uses zk-STARKs.
zk-SNARKs (Zero-Knowledge Succinct Non-interactive ARgument of Knowledge)
Zk-SNARKs enable the sender to provide proof that a send transaction occurred without revealing the transaction details, such as wallet addresses and transaction amounts. Zcash uses zk-SNARKs for its optional shielded transactions.
However, transactions that do not use this option appear on the blockchain in full detail, much like they would on Bitcoin or Ethereum. A 2022 network upgrade to Zcash removed the need for a trusted setup, making private transactions more accessible.
zk-STARKs (Zero-Knowledge Scalable Transparent ARgument of Knowledge)
Zk-STARKs represent an evolution of zk-SNARKs that simplify the process. zk-SNARKs require a complex initial setup between users, whereas zk-STARKs eliminate this trusted setup step by basing security on randomness. zk-STARKs, which are also seen as more scalable, have been adopted by some newer protocols, such as Aleph Zero. zk-STARKs are also used by the Ethereum Layer-2 blockchain, Starknet.
Mixers
Mixing protocols, such as CoinJoin, mix transactions to make it more challenging to identify senders, receivers, and transaction amounts. Think of it as a pool in which several senders and receivers participate, but in which it is difficult to know who sent coins to whom.
The Dash protocol uses a CoinJoin-style mixer for its optional PrivateSend transactions, bundling send transactions and ensuring the designated recipients receive the appropriate amount through Masternodes, which act as matchmakers.
Other wallet addresses involved in the CoinJoin are real participants, but also act as decoys to help disguise the breadcrumb trail common in other cryptocurrency networks. The end result is that it is not clear whether Person A sent funds to Person B; instead, Person A may have sent funds to Person C, Person D, or anyone else involved in the CoinJoin.
Of all of the common methods of obscuring transactions, Mixers have fallen under the most scrutiny from government agencies. In one high-profile case, the US Department of Justice charged the founder of the TornadoCash mixing protocol with transmitting criminal proceeds. In a similar case, the founders of Samourai Wallet were also charged with illegally running a money transmitting business.
Can Privacy Coins Be Tracked?
Advances in forensic techniques have made it possible to lift the veil on specific transactions and link private transactions to specific locations or wallet addresses. Firms such as Chainalysis and Elliptic look beyond the blockchain data to find clues based on IP addresses or transaction timing. Common workarounds include using a VPN or routing transactions through The Onion Router, a worldwide network of computers designed to protect user privacy by obscuring their IP addresses.
- IP Address Monitoring: By watching for transactions initiated from a specific IP address and then watching for time-correlated transactions on the blockchain, analysts may be able to link the transaction to the IP address and the wallet address of that user.
- Transaction Timing: Both Monero and Zcash have been vulnerable to transaction timing analysis. For example, with Monero, analysts could monitor the amount of time between a user creating a change output and spending the change, potentially linking the transactions to pinpoint a specific wallet address. However, both protocols have been patched or upgraded to combat this privacy risk. In Monero’s case, a mandatory ring size of 16 is now required, with the option to expand the ring size for greater privacy.
Best Privacy Coins Examples
When considering the best privacy coins, it’s important to weigh several factors, including tech features and the availability on crypto exchanges. While dozens of privacy coins exist, the following privacy coins list focuses on the leading projects in the space.
| Coin | Symbol | Market Cap |
|---|---|---|
| Monero |  XMR 0.52% XMR 0.52% |
$7.08B |
| Zcash (ZEC) | $4.65B | |
| Dash (DASH) | $555.34M | |
| Firo (FIRO) |  FIRO 2.13% FIRO 2.13% |
$25.35M |
| Grin (GRIN) | $3.83M | |
| Secret Network (SCRT) | SCRT | $42.4M |
| Beldex |  BDX +0.84% BDX +0.84% |
$811.91M |
| Decred | $343.43M | |
| Horizen |  ZEN +3.70% ZEN +3.70% |
$115.76M |
| Zano |  ZANO 0.69% ZANO 0.69% |
$133.56M |
Monero and Zcash, two of the oldest privacy coins out there, remain the largest ones by market cap, both exceeding $6 billion as of December 2025.
Both coins have recorded major gains in 2025 amid rising interest in privacy coins. The sector has been in the spotlight due to a growing need for financial privacy, which is often regarded as a direct response to the intensifying regulatory pressure and more advanced blockchain monitoring.
While Monero extended gains following its Fluorine Fermi upgrade to tackle spy nodes, Zcash has been the big surprise. It surged +765.78% over the past year to its highest level since January 2018.
One of the main catalysts behind Zcash’s recent growth was the halving event that occurred in November 2025, which reduced block rewards and lowered the annual inflation rate from 4% to 2%. Another driving factor is Grayscale’s application for a ZEC exchange-traded fund (ETF), which highlighted growing institutional interest in privacy coins.
Until an ETF is approved, traditional investors can gain exposure to ZEC through Cypherpunk Technologies Inc, a former biotech tech firm that rebranded in November 2025 to reflect its adoption of a crypto treasury strategy, purchasing over 200,000 ZEC tokens at an average price of $245. The company, formerly known as Leap Therapeutics, also completed a $58.8 million private placement led by Winklevoss Capital.
What Are Privacy Coins Used For?
Much like cash, privacy coins have both legitimate use cases and illicit use cases. However, illicit use cases may be overstated. While privacy coin opponents often cite the use of privacy coins in illicit activities, other cryptocurrencies like Bitcoin and Ethereum, and stablecoin tokens in particular, are used in far greater volumes for such purposes.
Meanwhile, some estimates suggest that less than one percent of all crypto volume is linked to illicit activity.
Legitimate Use Cases
Privacy coins have several legitimate use cases, including salary confidentiality, business IP protection, and private charitable donations. By design, most cryptocurrencies are permissionless and censorship-resistant. Anyone can perform a transaction, and, for the most part, transactions cannot be censored by a payment provider or financial institution. However, traditional blockchain networks introduce privacy concerns with their transparent ledgers.
- Salary Confidentiality: Workers who received crypto payments may prefer not to have their income documented on a public ledger.
- Business IP Protection: Businesses that interact with crypto may not want customers or vendors to know how much they hold in their wallets. Traditional crypto networks make this type of information easily accessible.
- At-Risk Activism: Although traditional crypto networks provide censorship-resistant transactions, activism-related support may draw political ire. Privacy coins offer an anonymous solution.
- Charitable Giving Under Oppressive Regimes: Privacy coins offer a way to support charities and causes without risk of confiscation by unfriendly governments.
Outside of these specific use cases, privacy coins often appeal to privacy-conscious people, regardless of the use case. Much like cash, privacy coins offer similar benefits due to their continued use for privacy and censorship resistance. An example sometimes given is: Would you like someone to trace your whole financial history simply because you used crypto at a supermarket register?
Illicit Use Cases
Although the use of privacy coins in illicit activities pales in comparison to major cryptocurrencies and stablecoin tokens, their ability to conceal transaction details makes them well-suited to illegal activity. On the other hand, privacy coins face liquidity challenges: they aren’t as easy to convert to cash.
Still, some privacy coins have seen illicit use cases, with Monero being the most common.
- Darknet Markets: From online drug markets, hacking tools, and stolen data, to far more sinister, darknet markets only accessible through special browsers are often powered by privacy coins like Monero. However, Bitcoin also remains popular in darknet markets due to its much higher liquidity.
- Ransomware: Bitcoin’s traceability has led to it falling out of favor for some ransomware attacks. Instead, victims are instructed to swap Bitcoin for Monero, sending Monero as a ransom payment due to its ability to conceal the receiving address.
Blockchain analytics firm Chainalysis has noted that many darknet markets and other illicit activities continue to be centered around BTC. However, bad actors can convert Bitcoin balances into privacy coins by using swaps and mixers to restore their anonymity.
Regulation, Bans & Government Visibility
As you might expect, privacy coins fall under regulatory scrutiny in many parts of the world, although responses have varied by region. Are privacy coins banned? Not yet, in most cases.
However, some countries, such as Japan, South Korea, Australia, and Dubai, have effectively banned privacy coins through regulatory measures that restrict trading. Let’s look at the privacy coin regulatory environment in several leading cryptocurrency markets.
EU AML Package
A new regulatory framework centered on Anti-Money Laundering (AML) will enact a full trading ban on privacy coins in the EU by July 10, 2027.
U.S. Treasury’s Stance
While privacy coins haven’t been banned in the US, some exchanges have delisted coins like Monero that enforce private transactions to avoid running afoul of regulators. In practice, the FinCEN Travel Rule remains the primary obstacle to trading privacy coins in the US, with crypto exchanges required to report and transmit details about the sender and receiver for transactions above $3,000.
Japan/Korea
Both Japan and South Korea enforce strict Know Your Customer (KYC) requirements on crypto exchange users. Similar to the US, withdrawals to private wallets pose a challenge for KYC compliance with privacy coins, effectively banning them from use.
By contrast, countries such as Switzerland, Portugal, Singapore, and parts of the Caribbean have adopted clear crypto regulations and view privacy as a right to be protected, rather than a risk to be eliminated.
Exchange Delistings Trend
Regulatory uncertainty and implicit bans have led many exchanges to delist several privacy coins. Kraken EU has delisted Monero and similar coins in some European countries, including Ireland and Belgium, in anticipation of stricter regulations. Similarly, Binance has placed several privacy coins on a monitoring list, signaling the potential delisting in specific markets.
The effect of privacy coin delistings is twofold: inefficient price discovery due to limited trading liquidity, as well as limited fiat off-ramps. Without an effective way to establish a value for privacy coins or a way to convert to other cryptocurrencies (or cash), privacy coins risk becoming isolated ecosystems with no connection to outside markets.
Can the Government See Your Crypto Wallet?
In most cases, yes. However, the cryptocurrencies you use and how you acquired them play a critical role in determining whether the government can identify your crypto holdings and match the transactions to you.
Transparent blockchains, such as Bitcoin and Ethereum, save a permanent record of each transaction on the blockchain, which is publicly visible. If you purchase Bitcoin through a KYC exchange, it’s possible to link your identity to a specific wallet address. However, it’s not possible to know for sure whether other wallet addresses belong to you.
On the other hand, if you create a Bitcoin wallet and someone sends you Bitcoin for providing a service, there’s no direct link between your wallet and your real-world identity. The wallet and its transactions are visible, but not necessarily linked to you.
By contrast, many privacy coins obscure the transaction history. For example, even if someone knows you hold Monero, it’s not currently possible to link you to your transactions with 100% certainty.
Risks, Limitations & Ethical Considerations
Privacy coins bring obvious benefits in their cash-like characteristics. However, they also come with some additional challenges, and viable privacy technology today may not remain so in the future. Let’s discuss some considerations to weigh and the practical limitations of using privacy coins.
- Traceability Arms Race: For the most part, privacy coins enable anonymous transactions. However, deanonymization studies have uncovered vulnerabilities with older protocols. For instance, Monero increased its minimum ring size to 16 in response to potential deanonymization threats posed by smaller rings. Transaction timing and decoy selection remain potential risks for deanonymization.
- Reduced Liquidity: With much lower adoption rates than larger cryptocurrencies like Bitcoin and Ethereum, privacy coins see lower trading liquidity. This leads to more erratic price movements and wider spreads, affecting their effectiveness as a store of value for peer-to-peer transactions.
- Regulatory Crackdowns: Sudden crypto exchange delistings can leave traders without a way to convert privacy coins to other cryptocurrencies or traditional currencies. The trend is clearly moving in the direction of more regulation that will affect privacy coins, if not outright bans.
- Reputation Risk for Businesses: Institutions and businesses that interact with privacy coins may suffer reputational damage due to (often unfair) association with illicit activities. Traditional banks may also shy away from businesses that transact in privacy coins, labeling the business as high risk and possibly even closing existing accounts.
- Blockchain Integrity Risks: Most privacy coins use either Proof of Work, Proof of Stake, or a variant to validate transactions. While larger decentralized networks make these consensus mechanisms viable, a 51% attack on Monero in 2025 demonstrated that smaller networks remain vulnerable to attacks that can alter transactions and perhaps even render the cryptocurrency worthless.
- Limited Use Cases: Although some privacy coin projects support smart contracts or plan to build support, their primary use case centers around peer-to-peer transactions. With lower adoption than Bitcoin, Ethereum, and other large projects, privacy coins remain a niche sector without mainstream retail use cases.
The Future of Privacy Coins
The future of privacy coins as a viable payment method and store of value hinges upon several factors. These range from technical innovation to determining who wins the regulatory tug-of-war between stricter KYC requirements and the rising demand for digital privacy.
The ongoing viability of privacy coins depends on their ability to develop solutions to emerging threats to user privacy, as well as the next moves by regulators. Leading privacy coin projects are addressing the cat-and-mouse privacy challenge through technological upgrades.
Some focus on zero-knowledge rollups, which represent a broader trend in the crypto space, expanding to both Layer-1 and Layer-2 chains, such as zkSync. This scaling solution bundles thousands of transactions into a single proof, offering better scalability and enhanced privacy without sacrificing security.
On the regulatory front, expect governments to continue restrictions based on Anti-Money Laundering / Countering the Financing of Terrorism (AML/CFT) initiatives. However, tax revenue may also be a driver for identifying crypto users.
Despite all challenges, the growing demand for financial privacy and autonomy using trustless networks has fueled cryptocurrency’s growth as much as speculation. Institutional players can influence the sector by adopting privacy-focused blockchains, particularly those that utilize zero-knowledge proofs. These may allow compliance with regulations while protecting proprietary data.
The winner of this tug of war may depend on where people live, with a clear move toward stricter regulation in many parts of Europe. In the US, SEC lawsuits and high-profile prosecutions of mixer protocol founders have had a chilling effect on access to crypto-related services, many of which block access by IP address.
How to Buy, Store & Spend Privacy Coins Safely
Although some exchanges have delisted specific privacy coins, many platforms still offer specific coins for trading. We listed centralized exchanges that support various privacy cryptos in the table earlier in the guide.
Other options to buy privacy coins include decentralized P2P exchanges, direct P2P swaps, and cross-chain bridges. Let’s discuss the ways to buy privacy coins, storage options, and best practices when using privacy cryptocurrency.
Finding On-Ramps in 2026
Buying privacy coins has become more challenging due to regulatory pressure; however, they are still accessible through peer-to-peer (P2P) transactions and cross-chain bridges.
- Decentralized P2P Exchanges: Platforms like Bisq and Haveno provide a decentralized platform that enables buyers and sellers to transact using a non-custodial escrow that allows people to transact with relative safety. Bisq provides a star rating for buyers and sellers. These platforms allow buyers and sellers to transact without KYC identity verification.
- Cross-Chain Bridges: The Secret Network supports bridging ETH and a variety of ERC-20 tokens from the Ethereum blockchain to acquire SCRT. The project also offers bridges from BNB Smart Chain and the Cosmos ecosystem.
- Anonymous in-wallet crypto exchange with no KYC requirements
- Trade thousands of coins across 60+ blockchains with low fees
- Beginner-friendly interface with numerous payment options
Privacy Coin Storage
Many privacy coins offer their own “official” crypto wallet, and well-established projects like Monero have several wallet options, including hardware wallets. Let’s discuss some popular wallet options for Monero.
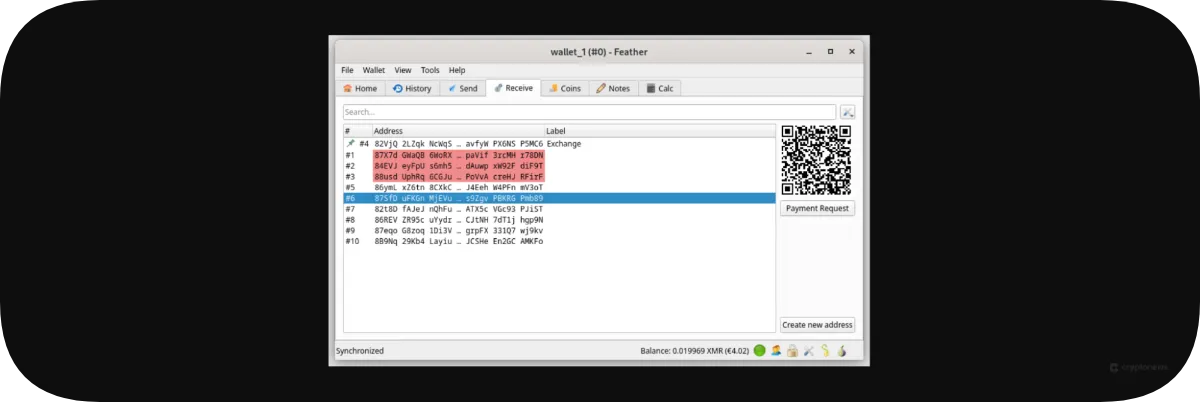
- Desktop: The Feather Wallet for Monero offers a cross-platform solution for storing Monero and supports both Trezor and Ledger hardware wallets if needed. The app is open-source, promoting transparency, and features a simple yet powerful interface. The app also supports TOR (The Onion Router), which we’ll discuss in more detail in the OPSEC tips.
- Mobile: Cake Wallet is one of the more popular mobile wallets for Monero and other cryptocurrencies. Like Feather Wallet, Cake Wallet supports TOR to protect your anonymity when making transactions. The app also supports Ledger hardware wallets via Bluetooth or USB-C (Android only).
- Hardware Wallets: Two of the leading hardware wallet makers support Monero: Ledger and Trezor. Hardware wallets store the wallet’s private keys offline, protecting against online threats. These wallets can connect with software wallets, such as the Feather Wallet, providing an intuitive interface while securely storing the private keys offline.
Operational Security (OPSEC) Tips for Privacy Coins
Many privacy coin users take a belt-and-suspenders approach to preserving their anonymity, using tools like VPNs or Tor to mask their IP address. Let’s examine some best practices for protecting your privacy.
- TOR: The Onion Router (TOR) is a worldwide network of computers designed to mask the IP address of the user. For example, maybe you’re in Albuquerque, New Mexico. With Tor, your connection hops through several computers, and you appear to be somewhere else, like France, for instance.
- VPN: Virtual Private Networks (VPNs) offer another alternative. In this case, your connection uses a secure “tunnel,” accessing internet resources through a remote server. Be aware that many VPNs are paid services, and some may retain connection logs.
- Fresh Addresses: Crypto networks use wallet addresses as your identity on the network. However, using the same wallet address for multiple transactions can leave a breadcrumb trail for others to follow. Consider using new wallet addresses for each transaction. Many wallets support this feature automatically, and the Monero protocol creates new addresses by default for receiving funds.
- Avoid Doxxing Metadata: The remaining OPSEC tips center on not revealing information that could connect your real-world identity to your crypto transactions.
-
- Beware of KYC exchanges: Using a KYC exchange that requires identity verification may enable government agencies or others with access to your exchange account to link your identity to a specific wallet address.
- Don’t Post Your Wallet Address: Avoid posting your wallet address online where your name can be associated with it. Even if that wallet is low on funds, it may be linked to other wallet addresses you own.
- Transaction Memos: Be careful about the information you include in optional transaction memos. These memos appear on the blockchain. Monero encrypts memos by default.
Final Thoughts on Privacy Cryptocurrencies
Privacy coins promise the same level of anonymity as cash, but in a digital form. Unlike Bitcoin and other major cryptocurrencies, privacy coins allow you to transact without creating a breadcrumb trail to analyze. However, this anonymity isn’t absolute, and several factors could compromise it, potentially leading to deanonymization.
While the networks themselves provide privacy features, a good part of protecting your financial autonomy and privacy comes down to the actions you take. Following best practices to protect your anonymity, such as using VPNs or TOR, using new wallet addresses for each transaction, and avoiding doxxing events, can make your privacy crypto use more secure.
Before investing in privacy coins, consider the viability of each project and the actions it has taken to stay ahead of privacy threats. Also, consider the size of the community, the use cases for each coin, and the on- and off-ramps available to you if you need to buy more or reallocate your position.
👉 Learn More: Crypto Accounts Purged: EU Imposes Anonymous Wallet Ban on 1 July 2027
FAQs
What makes privacy coins unique?
Can privacy coins be tracked?
Is Bitcoin a privacy coin?
Which crypto is truly anonymous?
What is the most popular privacy coin?
Are all cryptocurrencies anonymous?
References
- What are zk-SNARKs? (z.cash)
- Fundamentals: What Are Zero-knowledge Proofs? (alephzero.org)
- Founder Of Tornado Cash Crypto Mixing Service Convicted Of Knowingly Transmitting Criminal Proceeds (justice.gov)
- Founders Of Samourai Wallet Cryptocurrency Mixing Service Plead Guilty (justice.gov)
- 2025 Crypto Crime Report (trmlabs.com)
- 2025 Crypto Crime Trends (chainalysis.com)
- Vitaik.eth (etherscan.io)
- Stealth Address (getmonero.org)
- ZecHub Dashboard (zechub.wiki)
- Shielded Pools (zechub.wiki)
- Mimblewimble (beam.mw)
- Aleph Zero Business Whitepaper (alephzero.org)
- The New EU AML Package (deloittelegal.de)
- Funds “Travel” Regulations Questions & Answers (fincen.gov)
- Explained: The Monero 51% Attack (halborn.com)
- Roadmap (getmonero.org)
- The halo2 Book (github.io)
- Make Any Blockchain Token Private (scrt.network)
- Cypherpunk Technologies Inc rebrand (PR Newswire)
About Cryptonews
Our goal is to offer a comprehensive and objective perspective on the cryptocurrency market, enabling our readers to make informed decisions in this ever-changing landscape.
Our editorial team of more than 70 crypto professionals works to maintain the highest standards of journalism and ethics. We follow strict editorial guidelines to ensure the integrity and credibility of our content.
Whether you’re looking for breaking news, expert opinions, or market insights, Cryptonews has been your go-to destination for everything cryptocurrency since 2017.

















 Ryan Glenn
Ryan Glenn 
 Camila Karam
Camila Karam 
