Public vs. Private Keys: What Is the Difference?
Public and private keys play a crucial role in the security of your crypto assets, meaning that every investor must understand the differences. These keys are fundamental components of asymmetric cryptography, which is used to secure transactions and communications.
Learning the intricacies is essential for anyone involved in cryptocurrency trading, digital security, or blockchain technology. As such, this guide will detail the dynamics of public key vs. private key cryptography and explain how to find and safely store them.
Summary: Public vs. Private Keys
- Public Keys: Used for receiving transactions, openly distributed.
- Private Keys: Used for signing transactions, must be kept secret.
- Role: Public keys encrypt data; private keys decrypt data.
- Verification: Public keys verify digital signatures; private keys create them.
The distinction between public and private keys highlights their complementary roles in cryptographic systems. Public keys allow for open communication and transaction initiation, while private keys ensure that only authorized users can complete these transactions.
What Is Cryptography?
Cryptography is the practice and study of techniques for securing communication and data in the presence of adversaries. It involves the use of mathematical algorithms and protocols to ensure the confidentiality, integrity, and authenticity of information.
Public key cryptography and private key cryptography are both a part of asymmetric cryptography, which uses a pair of keys for encryption and decryption.
The field of cryptography has evolved significantly over the years, particularly with the advent of digital technologies and the internet. Modern cryptography employs complex algorithms and key management techniques to secure data in various applications, including email encryption, secure communications, and blockchain technology.
The use of public and private keys is central to many cryptographic protocols, ensuring secure and trustworthy digital interactions.
What Is a Public Key?
A public key is a cryptographic code that allows a user to receive cryptocurrencies or other forms of encrypted data. It is one-half of a cryptographic key pair and is intended to be shared openly.
Public keys are used to encrypt data, which can only be decrypted by the corresponding private key. Public keys play a crucial role in ensuring the transparency and security of transactions in blockchain networks. They enable users to generate addresses where they can receive cryptocurrencies and other digital assets.
Additionally, public keys facilitate secure communication in various online services, such as encrypted messaging and secure file sharing, by allowing users to exchange encrypted data confidently.
How Do You Find a Public Key?
Public keys are often derived from a user’s private key using cryptographic algorithms. In cryptocurrency wallets, the public key is generated automatically when a new wallet is created.
Users can find their public keys in their wallet settings or receive them directly when generating a new address for transactions.
Typically, public keys are displayed as a long string of alphanumeric characters or as a QR code, making it easy for users to share them with others.
Now you understand how to find a public key, let’s look at what is a private key.
What Is a Private Key?
On the other hand, a private key is a secret cryptographic code that is used to sign transactions and access the data or cryptocurrencies associated with a public key. It must be kept secure at all times, as anyone with access to the private key can control the assets linked to the corresponding public key.
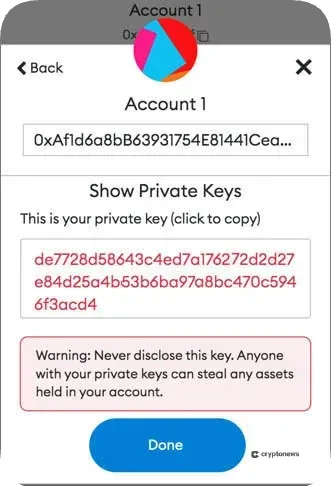
Private keys are the cornerstone of personal security in the digital world. They grant the holder full control over their associated assets and data. For this reason, safeguarding private keys against theft, loss, or unauthorized access is paramount. Failure to protect a private key can result in the irreversible loss of funds or sensitive information, highlighting the need for robust security practices.
How to Safely Store Your Private Keys
- Hardware Wallets: Use physical devices to store keys offline.
- Paper Wallets: Print keys on paper and store them securely.
- Encrypted Storage: Store keys in encrypted digital formats.
- Backup: Create multiple backups and store them in different secure locations.
Storing private keys securely involves using methods that minimize the risk of unauthorized access. Hardware wallets, for instance, are resistant to online hacking attempts, while paper wallets ensure keys are kept offline. Private key encryption regularly involves updating and securely storing backups to prevent loss due to physical damage or other unforeseen events.
How Are Public and Private Keys Related?
What are private keys in crypto, and how are they related to public keys? Public and private keys are mathematically linked pairs used in asymmetric cryptography.
The public key can be shared with anyone, while the private key is kept secret. Together, they ensure secure communication and transactions, as data encrypted with a public key can only be decrypted by the corresponding private key.
This relationship ensures that users can freely share their public keys to receive transactions or messages without risking their private keys.
The mathematical link between the keys means that the security of the system relies on the secrecy of the private key. As long as the private key remains confidential, the associated public key can be used openly and securely in various applications.
The Differences Between Public and Private Keys
There are a variety of differences between public and private keys, from their accessibility to types of encryption and verification methods. Let’s take a look at some of these differences.
Openly Available vs. Secret
The fundamental difference between public and private keys lies in their intended usage. Public keys are meant to be openly shared, allowing others to send encrypted data or funds to the key owner. In contrast, private keys are confidential and used exclusively by the owner to decrypt data and authorize transactions, maintaining the security of the digital assets or information.
Encryption vs. Decryption
In asymmetric cryptography, the process of encryption and decryption is split between the public and private keys. Public keys are used to encrypt data, ensuring that only the holder of the corresponding private key can decrypt and access it.
This separation of functions enhances security by ensuring that data can be shared publicly while remaining accessible only to the intended recipient. Recently, meme coin Shiba Inu raised $12 million to create a new network that utilizes Fully Homomorphic Encryption (FHE) that limits the need for decryption.
Verifying vs. Creating Digital Signatures
Lastly, digital signatures are a crucial aspect of asymmetric cryptography, providing a way to verify the authenticity and integrity of a message or transaction. Private keys are used to create digital signatures, while public keys verify them. This process ensures that the data has not been tampered with and confirms the identity of the sender, making it an essential component of secure communications and transactions.
Pros and Cons of Public Key Encryption
Now that we have a better understanding of the differences between public-private key mechanics, let’s explore the upside and downside of each.
Pros of Public Keys
Starting with the pros, here are some of the key benefits of public key encryption.
- Security: Enhances security by allowing only the private key holder to decrypt data.
- Authentication: Enables authentication of transactions and communications.
- Scalability: Suitable for large-scale systems and decentralized networks.
Simply put, public key encryption provides a robust framework for securing data and verifying identities. Its scalability makes it ideal for use in blockchain networks and other decentralized systems. Additionally, the ability to authenticate transactions and communications using digital signatures enhances trust and reliability in digital interactions.
Cons of Public Keys
- Complexity: More complex to implement than symmetric key encryption.
- Resource-Intensity: Requires more computational power for encryption and decryption.
Despite its advantages, public key encryption has some drawbacks. The complexity of implementing asymmetric cryptographic systems can be a barrier for some users or applications. Additionally, the computational resources required for encryption and decryption can be significant, especially in systems with high transaction volumes or stringent performance requirements.
Pros and Cons of Private Key Encryption
Let’s move on and look at the pros and coons of having a Bitcoin private key.
Pros of Private Keys
From our research, these are the key benefits of using encryption such as a Metamask private key.
- Control: Provides complete control over assets and transactions.
- Security: Ensures that only the key holder can authorize transactions.
- Authentication: Essential for creating digital signatures and proving ownership.
Private key encryption offers unparalleled control over digital assets and transactions. The ability to create digital signatures provides strong authentication, ensuring that only the key holder can authorize actions. This level of control and security is crucial for maintaining the integrity and trustworthiness of blockchain networks and other secure systems.
Read our guide on the best crypto wallets to find options on secure places to store your crypto.
Cons of Private Keys
- Vulnerability: If compromised, assets can be stolen without recourse.
- Management: Requires careful management and secure storage.
The primary downside of private key encryption is the risk of key compromise. If a private key is lost or stolen, the associated assets can be accessed by unauthorized parties. Managing and securely storing private keys is therefore essential to prevent such vulnerabilities. Users must employ robust security measures to protect their private keys from theft or accidental loss. According to a recent report, hackers used stolen private keys to steal over $1 billion worth of cryptocurrencies.
Conclusion
Public and private keys are fundamental to the security and functionality of digital transactions and communications.
Understanding their roles and differences is crucial for anyone involved in the digital economy. By utilizing these keys correctly, you can ensure your data and assets are securely stored and protected from potential outside attacks.
This is especially vital as the use of cryptocurrencies and other digital assets continues to grow, meaning that the importance of understanding and effectively using public and private keys cannot be overstated.
FAQs
What is an example of a private key?
What is an example of a public key?
How do I know if my key is public or private?
What happens if your private key is made public?
Can two people have the same public key?
References
About Cryptonews
Our goal is to offer a comprehensive and objective perspective on the cryptocurrency market, enabling our readers to make informed decisions in this ever-changing landscape.
Our editorial team of more than 70 crypto professionals works to maintain the highest standards of journalism and ethics. We follow strict editorial guidelines to ensure the integrity and credibility of our content.
Whether you’re looking for breaking news, expert opinions, or market insights, Cryptonews has been your go-to destination for everything cryptocurrency since 2017.
















 Ines S. Tavares
Ines S. Tavares 
 Camila Karam
Camila Karam 
 Ihssan El Medkouri
Ihssan El Medkouri 
 Anatol Antonovici
Anatol Antonovici