Crypto Identity Theft: What is It and How to Protect Yourself?
We believe in full transparency with our readers. Some of our content includes affiliate links, and we may earn a commission through these partnerships. However, this potential compensation never influences our analysis, opinions, or reviews. Our editorial content is created independently of our marketing partnerships, and our ratings are based solely on our established evaluation criteria. Read More
In 2024, US adults lost $47 billion to identity theft fraud and scams. Our team is well aware that this type of cyber threat is also on the rise in the crypto world, so we created this extensive guide to help you stay safe. We’ll explain what crypto identity theft is, how it works, and how it differs from traditional hacks.
You’ll also learn how to recognize the signs of identity theft, the best ways to protect yourself, and what to do if you’ve fallen victim to this type of fraud.
We approached the topic by analyzing real-world incidents and the newest security trends. The result is a practical guide that covers all aspects of identity theft in the crypto space, after which you’ll have all the tools you need to protect your digital assets and personal information.
 NordProtect – Editor's Choice for Crypto Identity Protection
NordProtect – Editor's Choice for Crypto Identity Protection
- Protect yourself from identity theft with 24/7 dark web monitoring
- Receive actionable security alerts and notifications
- Get up to $1M to cover identity theft recovery costs
What is Identity Theft in Crypto?
Crypto identity theft is a type of financial fraud that involves stealing personal information from crypto holders with the aim of gaining unauthorized access to their funds. In other words, the goal of attackers is to steal your private keys, biometric data, and login credentials to get а hold of your crypto or create fraudulent accounts under your name.
To comply with the AML and CTF regulations, many centralized crypto exchanges require users to undergo a KYC verification process. This process includes collecting personal details, such as names, social security numbers, home addresses, and phone numbers. You may also need to submit a copy of your government-issued ID or passport.
Centralized exchanges store your personal data on their platforms. However, if hackers succeed in breaching their security systems, they’ll gain access to your personal information, which may lead to identity theft and, in turn, crypto theft.
One of the most recent cases related to stealing user data is connected to Coinbase. In May 2025, cybercriminals paid the exchange’s customer support agents to steal sensitive customer data. They planned to use this data to trick users into giving them access to their funds while pretending to be Coinbase’s customer support representatives.
The fraudsters managed to get their hands on names, addresses, phone numbers, emails, government ID images, and snapshots of the balances and transaction histories of Coinbase users. Fortunately, they failed to gain access to login credentials and 2FA codes.
Another example of an identity theft attack is tied to LinkedIn. Namely, in March 2024, a group of hackers from North Korea stole 4,502.9 BTC by posing as LinkedIn job recruiters. Attackers sent a malicious Python script to an employee of a crypto exchange, DMM, in the form of a pre-employment test, which allowed them to gain access to sensitive data.
However, crypto identity theft is different from traditional hacking:
Crypto Identity Theft vs. Crypto Hacking
Crypto identity theft refers to using a stolen identity to gain access to crypto holdings, while crypto hacking involves exploiting vulnerabilities in smart contracts, blockchains, or user devices to steal cryptocurrencies. In short, the former centers around stealing personal data (name, ID, email, address, login credentials, phone number) and using it to access crypto accounts, while the latter refers to a direct attack on technical systems and code.
For example, a crypto identity attacker will steal your personal information to create a fake account to gain access to your funds or lure other traders into revealing their personal information. On the other hand, crypto hackers will use malware to exploit vulnerabilities in smart contracts and code to steal your funds.
According to CertiK’s co-founder, Ronghui Gu, crypto attackers are switching from hacking to identity theft because:
Smart contracts or blockchain code itself was the weakest point, but now the attackers feel like the weakest points may come from human behavior rather than the code.
How Does Crypto Identity Theft Work?
Fraudsters steal personal information, such as your name, email, wallet address, and recovery phrase, to gain access to your funds. They can also use this information to create fake accounts on crypto exchanges and bypass KYC procedures. Identity theft in crypto usually starts with phishing – using fake websites to trick crypto traders into revealing their private keys or login credentials – and ends up with a full account takeover.
With that in mind, the most common identity theft attacks include social engineering attacks. According to statistics, 98% of cyber attacks involve some form of social engineering, which means manipulating users to reveal their personal information. On that note, attackers usually pretend to be crypto exchange representatives, who ask users to share their seed phrase or private keys or click on malware links. Social engineering attacks include phishing, vishing, and pretexting.
Phishing and Vishing
Phishing refers to creating fake websites or apps that fraudsters use to steal your seed phrases, login credentials, or personal data. A typical phishing scheme includes sending fake emails that appear to be legitimate, with messages that contain words that convey urgency.
For example, you might receive an email titled Immediate action required, Final notice, or Account compromised from a crypto exchange you’re using. These emails will contain links that lead to fake websites that closely mimic the real thing. If you click on these links and enter your information, fraudsters will take control of your account.

Besides phishing, scammers also use vishing or voice phishing. For example, fraudsters will call and ask you to share your personal information, pretending to be customer service agents. Keep in mind that legitimate crypto exchanges will never contact you or ask you to share your private keys.
Phishing and Vishing Stats
- According to CertiK, in 2024, phishing and private-key thefts accounted for nearly $2.36 billion in losses. Moreover, statistics show us that crypto hacks surged by 303% in the first quarter of 2025. That is, over $1.66 billion was stolen across 197 incidents. And the majority of losses are attributed to compromised wallets and phishing attacks.
- In 2023, Chirag Tomar managed to steal over $20 million through his fake websites that mimicked Coinbase. He created fake websites, such as CoinbasePro.com, to trick users into giving away their login credentials and 2FA codes.
- A sophisticated new supply-chain attack dubbed PoisonSeed includes emails that mimic login portals of major customer relationship management (CRM) platforms, such as Mailchimp, SendGrid, Hubspot, Mailgun, and Zoho. These emails usually contain fake seed phrases that victims are instructed to use to create a new wallet or migrate their funds. Once you deposit or transfer your funds to these wallets, fraudsters will drain them.
Pretexting
Pretexting is a social engineering attack that includes creating a scenario through which attackers try to lure victims to share their personal information. It includes different techniques, such as impersonation (pretending to be a customer service agent or a colleague), fake websites, and deepfake scams (AI-generated fake videos or audio messages that impersonate real people).
- The Nigerian Prince scam, or the 419 scam, is the best example of pretexting. This scam involves a scenario in which the fraudster presents as a high-ranking official (e.g., an exchange CEO). They then ask the victim to share their personal information or make an advance payment in return for rewards. The fraudsters usually collect enough personal data from both the victim and the impersonated official for the scam to work properly.
SIM-Swap Attacks
SIM-swap attacks (or SIM hijacking) involve porting the victim’s SIM card details to another card and taking control of their phone number in order to receive their calls and messages. To accomplish that, the attacker will call the victim’s mobile phone operator and pretend to be them by using previously collected personal data.
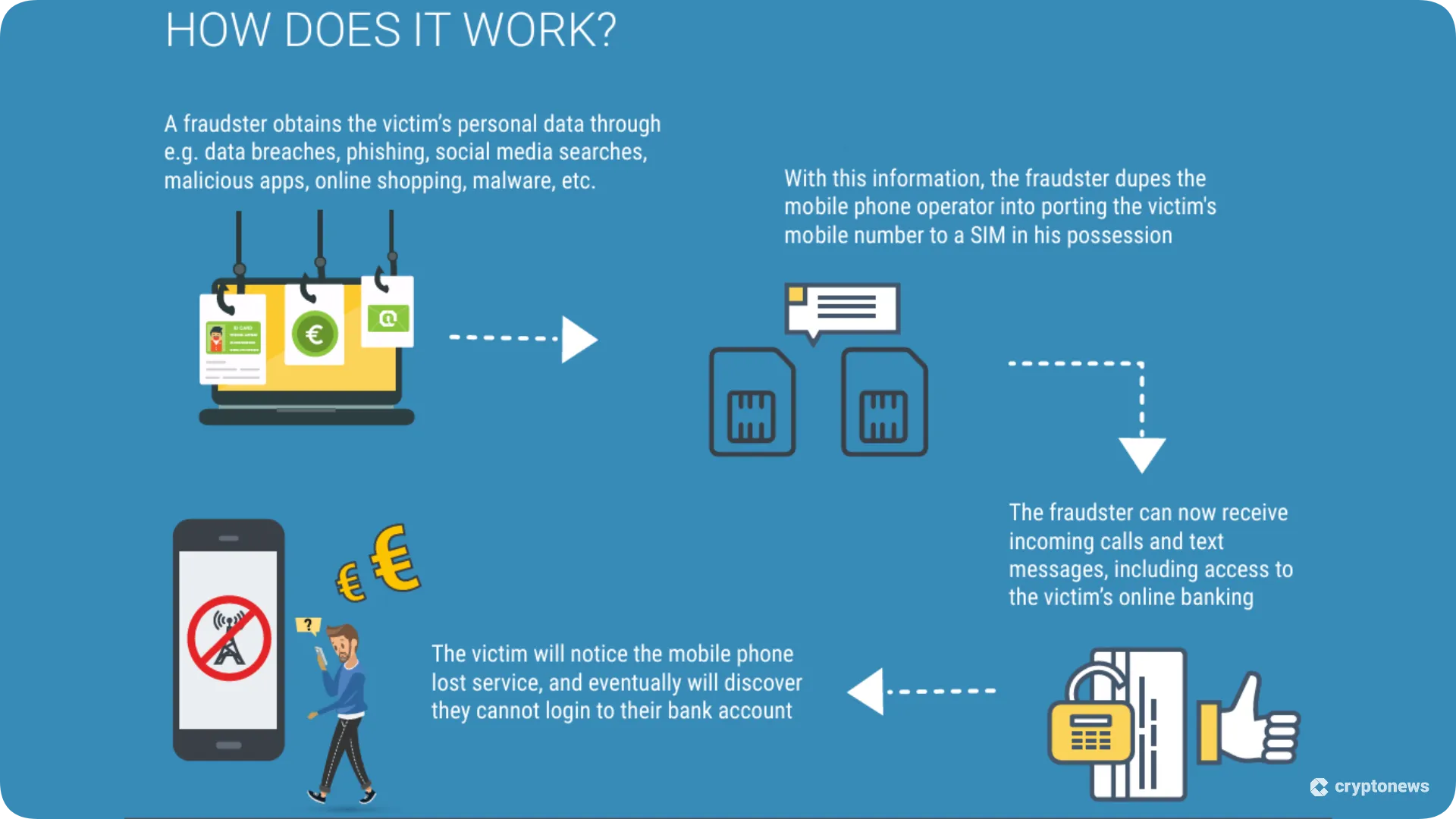
They’ll usually claim that they’ve lost their physical SIM card but want to keep the number. Once the victim’s phone number has been ported to a card controlled by the scammer, they’ll be able to receive SMS messages intended for the victim, such as two-factor authentication (2FA) codes used for access to crypto wallets or exchanges. This enables them to take control of their victims’ accounts and steal their funds.
In 2018, Ellis Pinsky, a high school student from New York, and his friends conducted a SIM-swap attack to steal nearly $24 million worth of crypto from an investor called Michael Terpin. They bribed an AT&T worker to do the SIM swap.
Synthetic Identity Theft
Synthetic identity theft refers to creating a false identity by combining real personal information, such as a date of birth or a social security number, with fabricated details, such as names and addresses. The idea behind this is to steal someone’s SSN to obtain a new one, i.e., to create a false identity.
Fraudsters steal social security numbers from people with no credit history and pair them with a fabricated name to create a fake identity. They will use these new identities to create accounts on crypto exchanges and bypass KYC procedures. They might also try to obtain loans or open lines of credit.
How to Protect Yourself from Identity Theft in Crypto
Now that you know what identity theft in crypto is and what can happen if hackers get hold of your personal information, you’re probably wondering if there’s a way to protect yourself from this threat. Luckily, there is. In this section, we’ll show you how to keep your crypto investments safe and your personal information away from prying eyes.
Choose Reputable Platforms
If you decide to become a crypto trader, make sure that the exchange you choose is reputable and trustworthy. On that note, give preference to well-established platforms that utilize strict security measures.
You should also choose decentralized exchanges over centralized ones since they won’t require you to share your personal information or go through the KYC verification process. Some of the best anonymous crypto exchanges with no KYC requirement include Best Wallet, Margex, and Blofin. Keep in mind that crypto exchanges are not banks, which means you should store the majority of your digital assets in crypto wallets, preferably cold wallets.
Crypto exchanges will never ask you to give out your personal information or share your private keys. Moreover, they will never call or text you, send you new seed phrases, or offer you a new wallet address to move your funds to.
Secure Your Account
Once you’ve chosen a reputable platform, it’s time to create an account. Needless to say, using strong and unique passwords is a must. You can create a strong password by combining letters, numbers, and symbols. Don’t use your personal information to create a password, and avoid using the same password across different accounts.
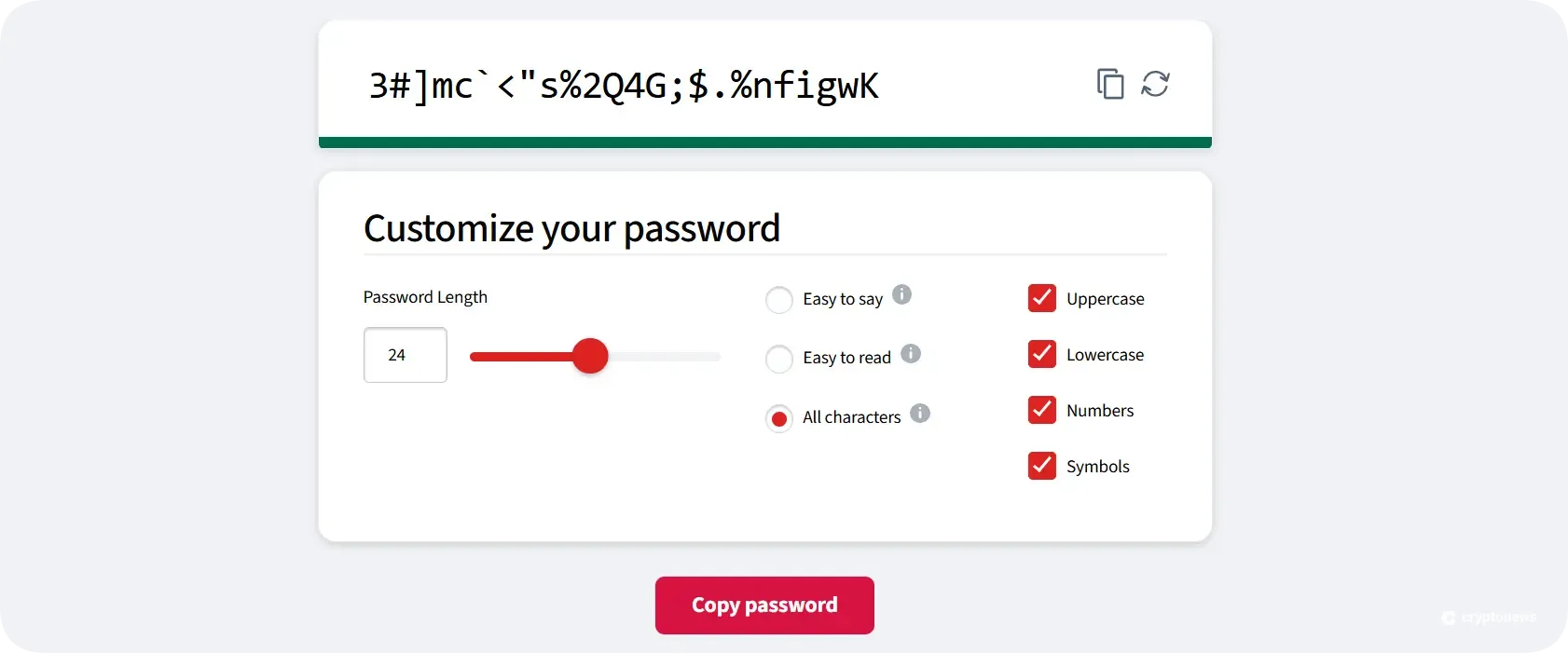
You can add an extra layer of protection by enabling two-factor authentication (2FA). However, avoid using SMS 2FA since you risk becoming a victim of SIM-swap attacks. Instead, use app-based 2FA solutions, such as Google Authenticator.
An example of a weak password: John12345
An example of a strong password: BYZ8hkd!lsEjP3nOA#w
Use a VPN
VPNs (Virtual Private Networks) are services that encrypt your Internet traffic and hide your online data by routing your connection through remote servers. This prevents hackers from collecting your personal information, such as location, IP address, traffic patterns, and more. VPNs also prevent hackers from intercepting sensitive data in transit, such as your private keys and login credentials.
The best VPNs for crypto trading, like NordVPN, also block suspicious URLs (which prevents phishing attempts) and have built-in ad blockers and antiviruses for an extra layer of protection.
Visit NordVPNInstall an Antivirus and Keep Your Software Updated
Antivirus software will detect and remove malware, Trojans, spyware, and adware from your devices, which will prevent hackers from stealing your personal information. Some antivirus providers also offer identity theft insurance plans. With that in mind, you should also update your software regularly since new viruses are released on a daily basis.
In 2024, Kaspersky, one of the most popular cybersecurity and antivirus providers, discovered an average of 467,000 malicious files per day.
Use Identity Protection Tools
Identity protection tools prevent hackers from stealing your personal data by combining multiple security features, such as monitoring, alerts, and recovery assistance. This means you’ll get notified if there’s suspicious activity, for example, someone trying to open an account using your login credentials. These tools can also include spam filters, antivirus software, anti-phishing protection, and password managers.
You should also opt for services that offer a dark web monitoring tool. One such tool is NordProtect, which will alert you if your personal information has been exposed on the dark web. NordProtect also includes an identity theft recovery service. If your identity is stolen, you may be reimbursed up to $1 million for eligible recovery expenses.
In 2024, there was a 15.4% increase in data exposure on the dark web, with more than 2,080,000 alerts. The most common and vulnerable types of data on the dark web include emails, passwords, usernames, phone numbers, and first and last names.
Visit NordProtectMonitor Your Account Regularly
By monitoring your account activity on a regular basis, you’ll be able to detect suspicious transactions, such as large withdrawals or deposits, or multiple small transactions. This will also help you prevent dusting attacks. If you receive tiny amounts of crypto (aka dust) that you didn’t request, and you transact with these coins, attackers can link your wallet addresses to your real identity and target you further.
Two weeks after the Litecoin halving (on Aug. 10, 2019), nearly 300,000 Binance Litecoin addresses received 0.00000546 LTC, which was a part of a large-scale dusting attack.
Don’t Click on Suspicious Links
If you receive a message that requires an urgent response, it’s most likely a scam. You should never click on suspicious links. Especially if the sender asks you to provide your personal information or share your private keys. You should also avoid sharing your personal details on social media, including your credit card numbers and pictures of your ID and password.
Real link example: https://accounts.binance.com/en/login?…
Phishing link example: https://www–binance.com/binance/login…
Consequences of Identity Theft in Crypto
Identity theft can lead to devastating consequences, from losing access to your account on crypto exchanges to losing your digital assets. Moreover, hackers can use your identity to create fake accounts and conduct criminal activities, which can ruin your reputation and get you in trouble with the law. Since crypto transactions are anonymous and irreversible, the chances that you’ll get your stolen funds back are close to zero.
With that in mind, the main consequences of identity theft include the following:
- Account takeovers: If scammers steal your identity, they’ll gain access to your login credentials and private keys. This means they’ll be able to log into your accounts on crypto exchanges, which will give them full control over your assets.
- Loss of funds: Once the attackers gain control over your account, they can sell your coins and tokens or transfer them to their wallets. Since crypto transactions are irreversible, you may never get your funds back.
- Inflow of scam emails and calls: Identity theft can lead to a surge of scam emails and calls. Why? Because your phone number and email may have been sold on the dark web.
- Reputation damage: If someone steals your identity, they can use your profile to share malware links, write misleading posts, or create AI-generated videos that impersonate you, which may ruin your reputation.
- Legal issues: Hackers can use your personal information to conduct criminal activities, which can result in legal issues and criminal charges.
How to Recognize Signs of Identity Theft
The following signs could be a hint that you’ve become a victim of crypto identity theft:
- Unexpected changes in your crypto balances
- Password reset requests that you didn’t initiate
- Locked-out accounts
- Getting contacted by creditors
- Being logged out of your account frequently
- Unfamiliar login attempts
- New accounts in your name
- Suspicious SIM-related alerts
By detecting the signs of identity theft early on, you’ll be able to stop it from happening:
What to Do if You’re a Victim of Identity Theft?
If you detect signs of crypto identity theft, the first thing you need to do is freeze your account. Most crypto exchanges have integrated options that will help you do that. However, if this option is unavailable, you must notify customer support about the suspected fraud.
Next, you need to change your passwords, enable 2FA, and monitor your account on a regular basis. You can also use NordProtect to remove your personal information from the web to prevent further attacks and secure your wallets.
What’s more, you must report the theft to authorities (file a report with the Federal Trade Commission) and place a fraud alert by contacting Experian, TransUnion, or Equifax. You can take advantage of identity theft recovery services, like the one offered by NordProtect, to cover your legal fees, credit reports, lost wages, document replacement, and mental health counseling.
The time required to recover from identity theft can last anywhere from 30 days to several years, depending on the severity of the fraud.
Conclusion: How to Protect Yourself From Identity Theft in Crypto
Due to their decentralized nature, cryptocurrencies have become a breeding ground for various forms of identity theft. The latest trends show us that fraudsters are switching from traditional hacks to social engineering attacks to exploit human weaknesses instead of the technical vulnerabilities of smart contracts.
On that note, attackers will try to steal your personal information by pretending to be crypto exchange representatives, high-profile people, or even your colleagues. The most common social engineering attacks include phishing, vishing, and pretexting.
You can protect yourself from crypto identity theft by choosing highly secure crypto exchanges, creating strong and unique passwords, enabling 2FA, and using identity theft protection services like NordProtect.
Visit NordProtectFAQs
How common is identity theft in crypto?
Is providing personal information to a crypto exchange safe?
What personal information is at risk in crypto?
References:
- Identity Fraud and Scams Cost Americans $47 Billion in 2024 (AARP)
- Protecting Our Customers – Standing Up to Extortionists (Coinbase)
- FBI Links North Korean Hackers to Largest Crypto Hack of 2024 (CNN)
- 16 Billion Apple, Facebook, Google And Other Passwords Leaked (Forbes)
- Social Engineering Statistics: How Can Your Business Avoid Being One? (Sprinto)
- Hack3d: The Web3 Security Quarterly Report – Q1 2025 (Certik)
- Consumer Protection Tuesday: How We Helped Take Down a $20M Spoofing Scheme That Exploited Coinbase’s Brand (Coinbase)
- PoisonSeed Campaign: New Supply Chain Phishing Attack Targets CRM and Email Providers (Check Point)
- The Nigerian Prince scam: Everything you need to know (NordVPN)
- Beware! Elon Musk deepfake livestream scams thousands with fake crypto scheme (CNBC)
- SIM-swapper gets 18 months, must pay back $20 million he stole from crypto investor (The Record)
- The cyber surge: Kaspersky detected 467,000 malicious files daily in 2024 (Kaspersky)
- Cyber attacks on the rise: data theft on the dark web up 15% in 2024 (CRIF)
About Cryptonews
Our goal is to offer a comprehensive and objective perspective on the cryptocurrency market, enabling our readers to make informed decisions in this ever-changing landscape.
Our editorial team of more than 70 crypto professionals works to maintain the highest standards of journalism and ethics. We follow strict editorial guidelines to ensure the integrity and credibility of our content.
Whether you’re looking for breaking news, expert opinions, or market insights, Cryptonews has been your go-to destination for everything cryptocurrency since 2017.













